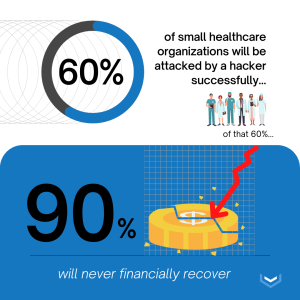
Did you know that 60% of small healthcare organizations will be successfully attacked during any given year? Furthermore- of that 60%- 90% will never be able to recover from the financial impact.
With data breaches skyrocketing to unprecedented heights, securing confidential information is more important now than ever. A HIPAA covered entity that stores, receives, or transmits Protected Health Information (PHI) needs to operate on a secured network server. If not, they are at high risk for a data breach.
Healthcare organizations are the most heavily targeted industry by hackers and cyber criminals. This also makes it the most strictly regulated industry in regards to data security. How can healthcare providers and other Covered Entities (CEs) protect their valuable information with data encryption? Keep reading to find out.
What is a Data Breach?
A data breach is a type of security violation. It occurs when unauthorized personnel gain access to information that is meant to be kept private. The files and documents accessed during a data breach are viewed and/or taken without permission. When organizations do not implement proper safeguards to protect confidential information, a hacker can easily access their network.

Before executing a successful data breach, a hacker will typically look for weaknesses in an organization’s security system. Then, the hacker will target those weaknesses to infiltrate their network. A hacker can use this confidential information to commit fraud, identity theft, and even blackmail. Common types of confidential data may include SSNs, banking information, employment records, and PHI.
Data Breaches in the Healthcare Industry
Data breaches can happen in any industry. However, they are particularly dangerous in the healthcare industry. PHI is an extremely valuable form of currency for a hacker because of its high value on The Black Market.
In fact, healthcare data can be up to 50 times more valuable than other types of confidential information. Thus, it is extremely lucrative for a hacker to target healthcare organization’s that store PHI.

In addition to its high Black Market value, PHI is also hyper personal. Unlike other kinds of sensitive information like banking records, medical records contain information that is extremely detailed and extensive. A complete and comprehensive overview of medical history can include their disease states, treatment plans, and list of prescribed medications. A hacker can use this information to black mail and extort someone for hundred and even thousands of dollars.
How to Prevent a Data Breach?
Any organization that stores patient data should always prioritize data security. For healthcare entities in particular, this is crucial, especially when maintaining HIPAA compliance.

Hacking incidents and data breaches are an unfortunate reality healthcare entities need to be aware of. After reading those shocking, and likely frightening, facts and statistics, you are probably wondering how to prevent this from happening. Even though there is an ever-increasing threat to data security, a solution has been established that significantly decreases this risk.
What is Encryption?
Encryption is a method used to secure confidential data. It is one of the most effective ways to keep data protected in transit and at rest. Using a complex algorithm, encryption strips data of all its identifiable factors. Therefore, it is rendered utterly useless to a hacker.

Encryption makes valuable, sensitive information look like nonsense. The only way to make it readable again is with a decryption key. This private key encrypts and decrypts the data. It should never be shared with anyone who does not need it. Additionally, decryption keys should be rotated and updated on a consistent basis to further prevent a data breach.
Encryption for Data at Rest & in Transit
Under The HIPAA Security Rule, data is split in two categories: data at rest and data in transit. The National Institute of Standards and Technology (NIST) established a set of standards for data in motion and data in transit. These standards for encryption depend on what state of motion the data is in.

Data at Rest is data that is not moving. It is information that is stagnant on a laptop, hard drive, or other type of electronic device. Encrypting data at rest is addressable under HIPAA. This means that person examining the data needs to determine whether it is reasonable and appropriate to encrypt the data.
While it may always be appropriate to encrypt data, it is not always reasonable. If the examiner decides to not encrypt the data, they are required to document their reasoning. Additionally, they need to consider and attempt alternative that would reduce the risk of a data breach.
Data in Transit is data that is moving. This type of data is traveling cross the internet on a network server. Standards for encrypting data in transit are required under HIPAA, meaning it must be secured no matter what.
How does Encryption Protect Data in Transit?
Healthcare providers often use electronic modalities to send health data because it is easy and convenient. However, the data within these electronic communication channels needs to be properly safeguarded with encryption.
Before this data is sent to its desired location, it travels across multiple network servers. An exact copy of this data is stored on each server it passes through. If these servers are not secured, they are highly susceptible a data breach.

Should a hacker gain access to these servers, they would also have access to all the data being stored there. This is where encryption becomes essential.
End-to-end data encryption keeps information anonymous even as it passes through network servers. The stored copies are completely anonymous when they are encrypted. So, even if the set is hacked, the encrypted data is useless because it means nothing without the decryption key.
Data Encryption for Healthcare Providers
In healthcare, data security is essential. Encryption is one of the best data security practices for healthcare providers. It keeps PHI secure, anonymous, and ultimately reduces the risk of a data breach. Data in transit is heavily regulated under The HIPAA Security Rule. As such, maintaining HIPAA compliance is crucial for a Covered Entity.

Having secure, encrypted data makes audits from the Department of Health and Human Services (HHS) seamless, efficient, and worry-free. With a HIPAA compliant data security company, you can rest assured that your sensitive information is properly safeguarded with encryption.

